Azure Logs Ingestion Event Destination
This guide covers how to send ngrok events including network traffic logs into Azure via the Logs Ingestion API.
This is useful if you want to keep an audit log of configuration changes within your ngrok account, record all traffic to your endpoints for active monitoring/troubleshooting, or leveraging it as a SIEM for security inspections.
By integrating ngrok with Azure, you can:
- Quickly identify application issues in real-time using ngrok request events using Azure logs processing.
- Historically audit changes occurring within an account. Be able to historically audit changes within an account.
- Profile usage of your service by using logs queries and real-time data analytics.
- Identify security issues by using ngrok events.
Step 1: Create a Log Analytics Workspace
These steps were adapted from the Create a Logs Analytics Workspace docs from Microsoft.
-
Using a browser, log into your Azure portal.
-
Navigate to the search bar and type in Log Analytics Workspaces
-
Click on the Services entry (not the Marketplace entry).
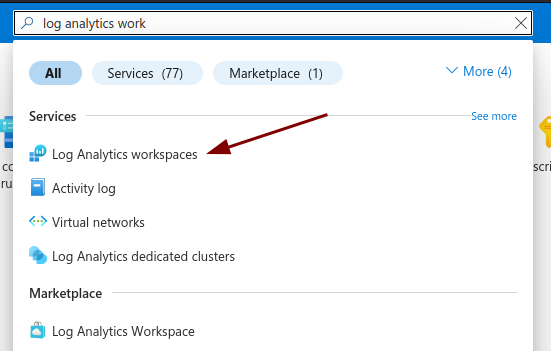
-
Click Create on the top bar Log Analytics Workspace page.
-
Follow the wizard to create your Log Analytics Workspace, filling in the necessary region information, name, and resource group, before clicking Review + Create. These values can be anything you like and do not impact ngrok's ability to send logs to your Azure account.
-
Click Create at the bottom of the review step to finally provision the Log Analytics Workspace.
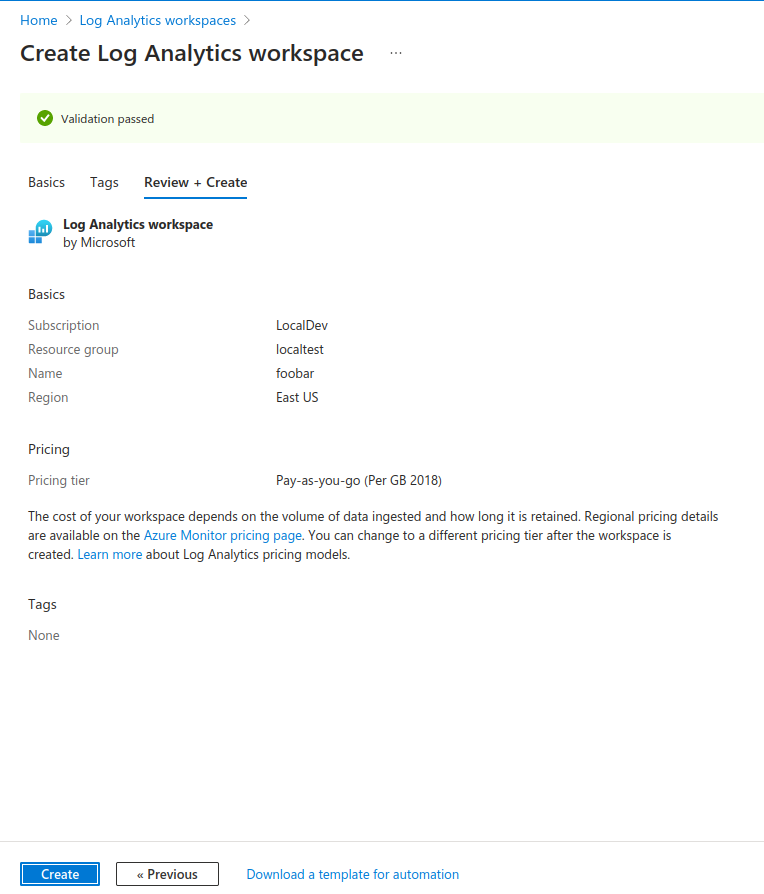
You now have a Log Analytics Workspace, which will be the home for your data collection endpoint, tables, and rules.
Step 2: Create a Data Collection Endpoint
These steps were adapted from the Create a data collection endpoint docs from Microsoft.
-
Navigate to the search bar and type in Data Collection Endpoints
-
Click on the Services entry.
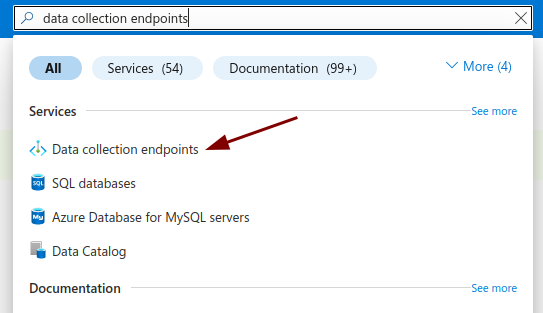
-
Click Create on the top bar Data Collection Endpoints page.
-
Follow the wizard to create your Data Collection Endpoint, filling in the necessary region information, name, and resource group, before clicking Review + Create. These fields can be anything you like and to not impact ngrok's ability to send logs to your Azure account.
-
Click Create at the bottom of the review step to provision the Data Collection Endpoint.
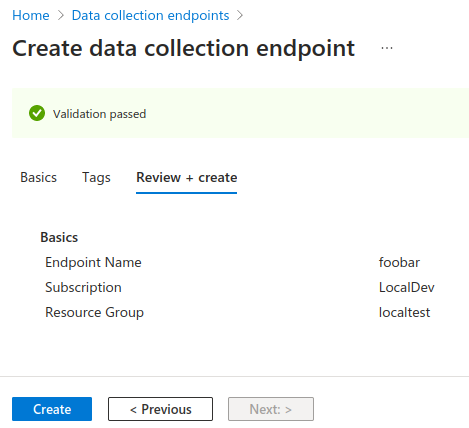
You now have a Data Collection Endpoint, which is the network accessible service that ngrok connects via to send events into Azure.
Step 3: Create a DCR-based Custom Table in the Workspace
These steps were adapted from the Create a new table in Log Analytics workspace docs from Microsoft.
-
Navigate to the Log Analytics Workspaces list once again.
-
Click the workspace you created previously in Step 1.
-
Navigate to Settings -> Tables in the sidebar menu of the selected workspace.
-
Click Create on the top bar, and select New custom log (DCR-based).
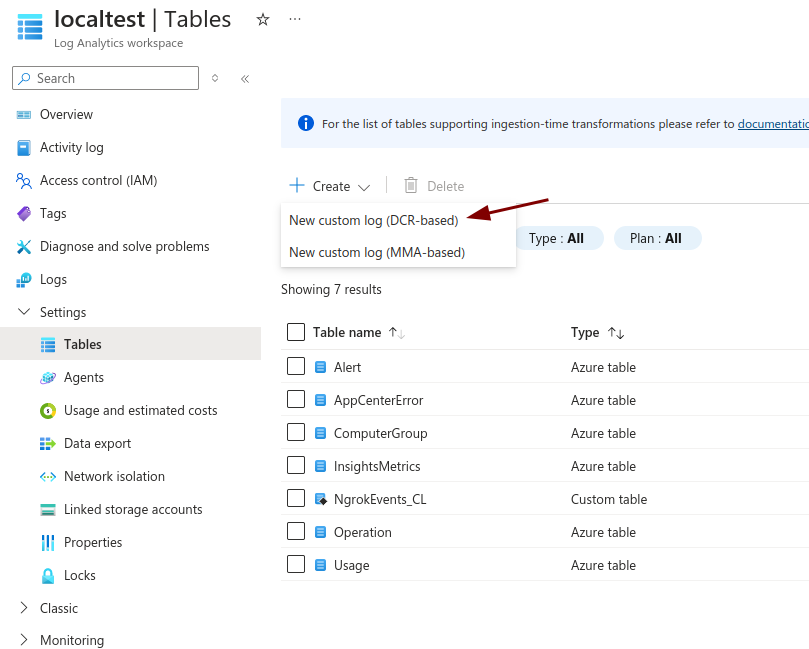
-
Populate the table name with a name of your choice and the DCE field with the existing DCE you created in Step 2.
-
Click Create a new data collection rule underneath the Data collection rule field, which opens a drawer. Fill out the resource group and name, before clicking Done on the drawer.
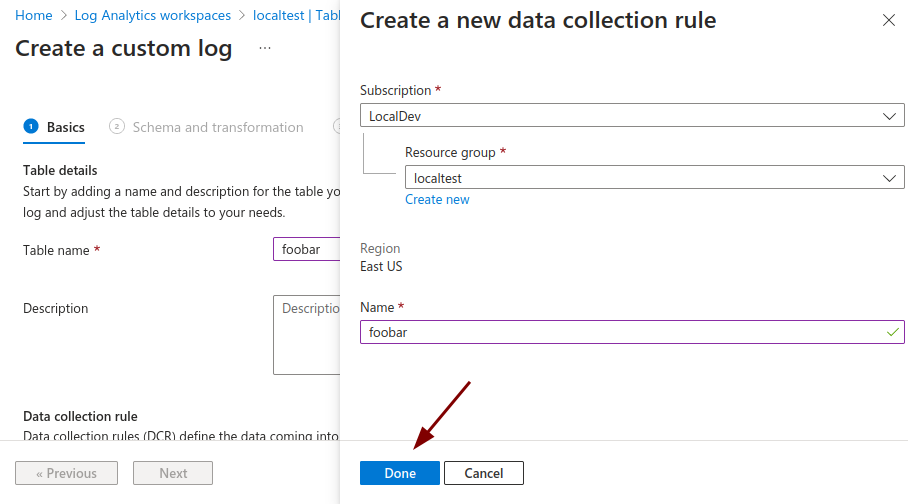
-
Click Next in the table creation wizard.
-
Upload the following json file using the wizard. After uploading, you will notice a warning header "TimeGenerated field is not found in the sample provided" which is expected.
Loading…
You will notice a warning header "TimeGenerated field is not found in the sample provided"; this is expected.
We will remedy this by using the Transformation Editor.
-
Click the Transformation editor button on the top bar of the wizard, which will open a drawer.
-
Paste in the following transformation and click Run.
Loading…
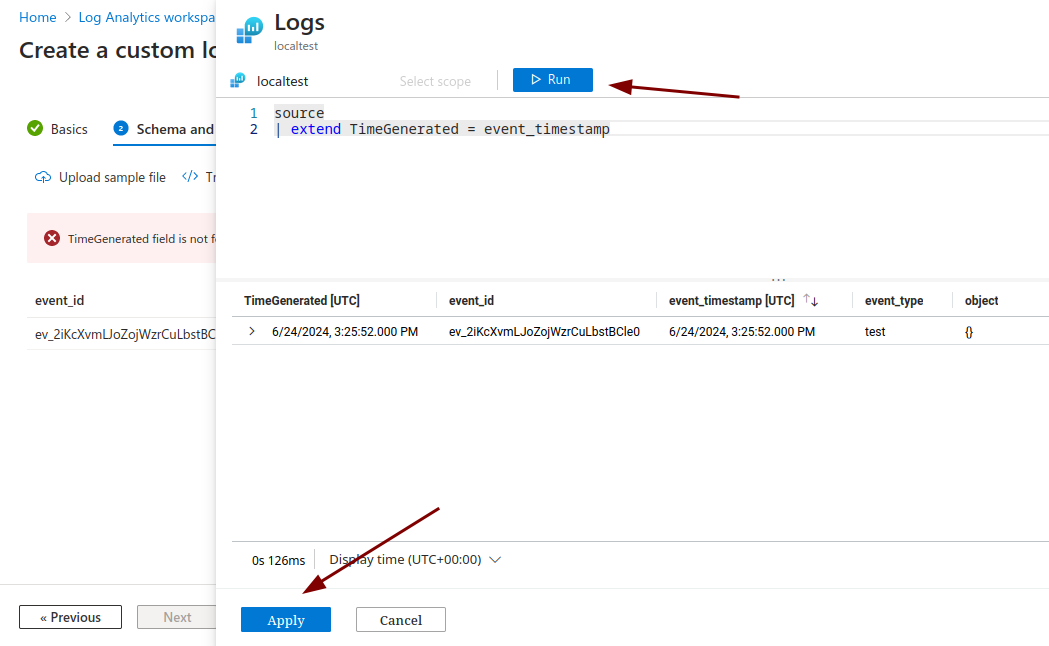
-
Click Apply.
-
Click Next.
-
Click Create.
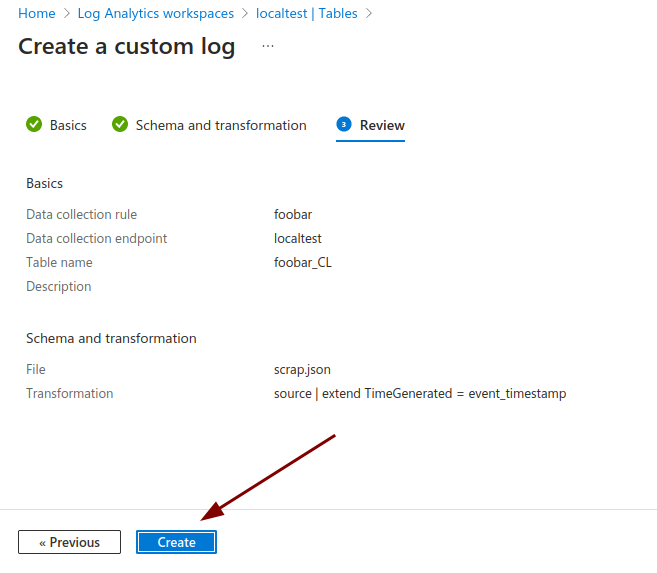
You now have a Data Collection Rule properly configured for ngrok events, alongside a table where the data will be stored.
Step 4: Create a Microsoft Entra Application
These steps were adapted from the Create a Microsoft Entra Application docs from Microsoft.
-
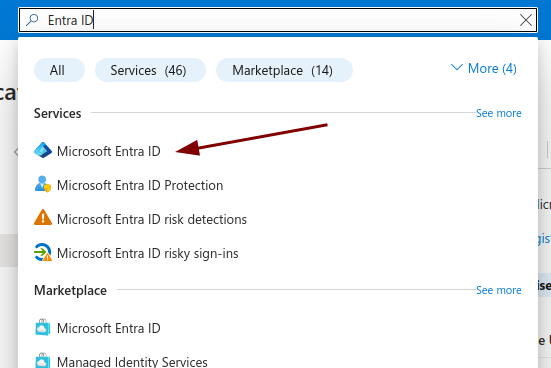
Navigate to the search bar and type in Microsoft Entra ID.
-
Select the Microsoft Entra ID under Services, not the Marketplace item.
-
Navigate to Manage -> App registrations on the sidebar.
-
Click New registration
-
Name the application ngrok-events or something similar to clarify its use; this entity will be what ngrok uses to authenticate with your data collection endpoint.
-
Select the first radio option, Accounts in this organizational directory only for the account type
-
Click Register
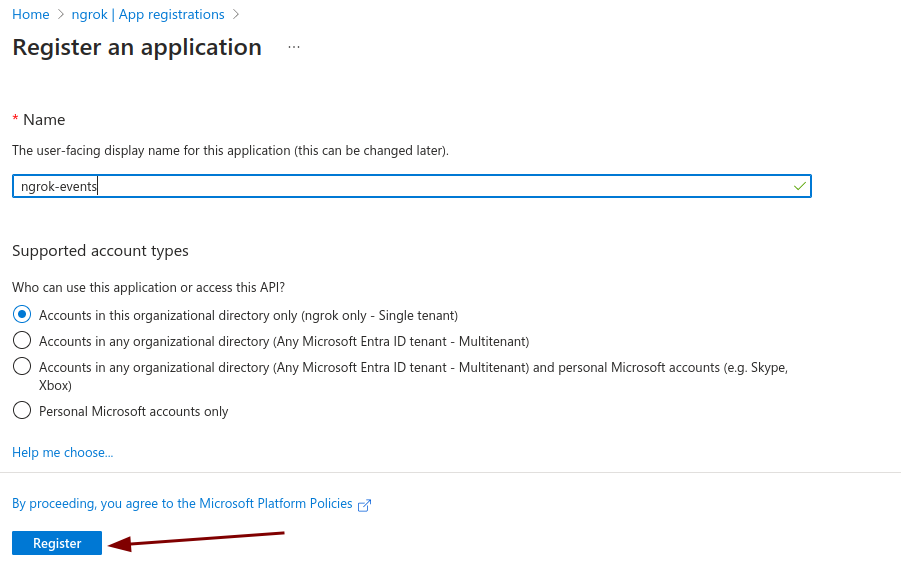
You have now created an Microsoft Entra ID App Registration, which is a service user construct that grants roles/access to services like ngrok.
Step 5: Assign IAM permissions to the Application for the DCR
These steps were adapted from the Assign permissions to the DCR docs from Microsoft.
-
Navigate to the search bar and type in Data collection rules.
-
Select the Data collection rules option under Services.
-
Click on the Data collection rule created in Step 3.
-
Click Access control (IAM) on the sidebar.
-
Click Add on the top bar.
-
Click Add role assignment.
-
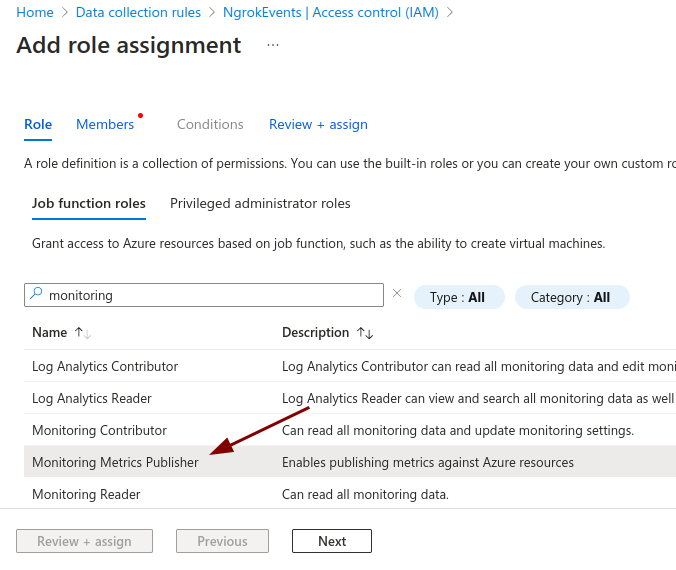
Search for Monitoring in the search bar underneath Job function roles.
-
Click on Monitoring Metrics Publisher.
-
Click Next, advancing to Members.
-
Click Select members.
-
Search for the app registration you created in Step 4.
-
Click on the service principal and click Select.
-
Click Review + assign.
-
Click Review + assign again, confirming the role assignment.
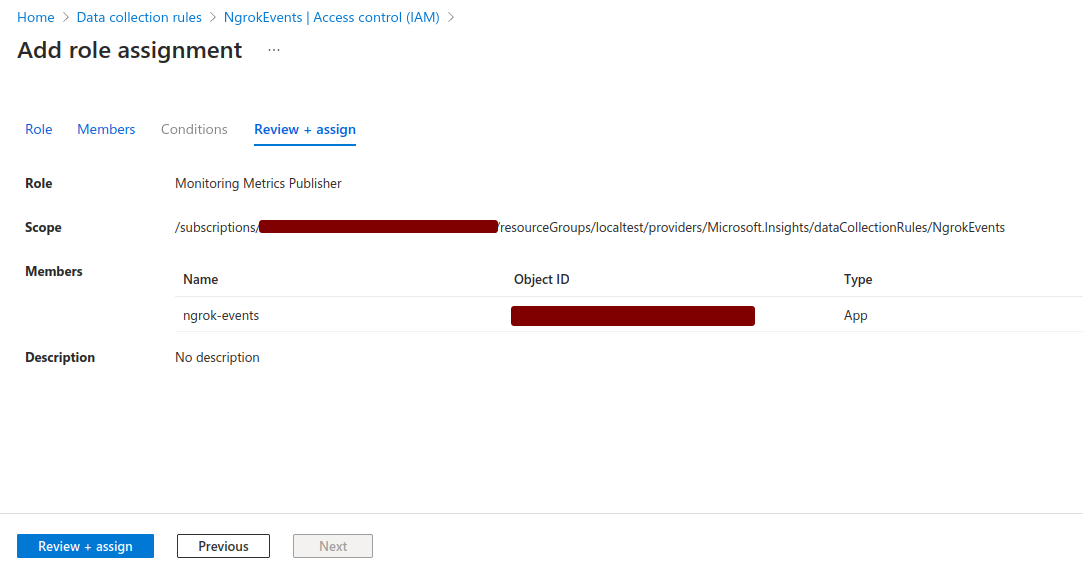
You have now granted access for the ngrok application to ingest logs into the DCR, which is the final step before we can create an Event Destination.
Step 6: Gather necessary data for Event Destination
In order to create an event destination in your ngrok Dashboard, we will need to gather the following information from what we just created in Azure:
- the Tenant ID
- the Application's Client ID
- the Application's Client Secret
- the DCR immutable ID
- the DCR stream name
- the DCE log ingestion URI
-
To gather the first three fields, we will navigate back to Microsoft Entra ID. Search for Entra in the top search bar and select the Microsoft Entra ID service.
-
Navigate to Manage -> App registrations in the sidebar, and select the application you created in Step 4.
-
Copy the Application (client) ID and Directory (tenant) ID from the Overview Page.
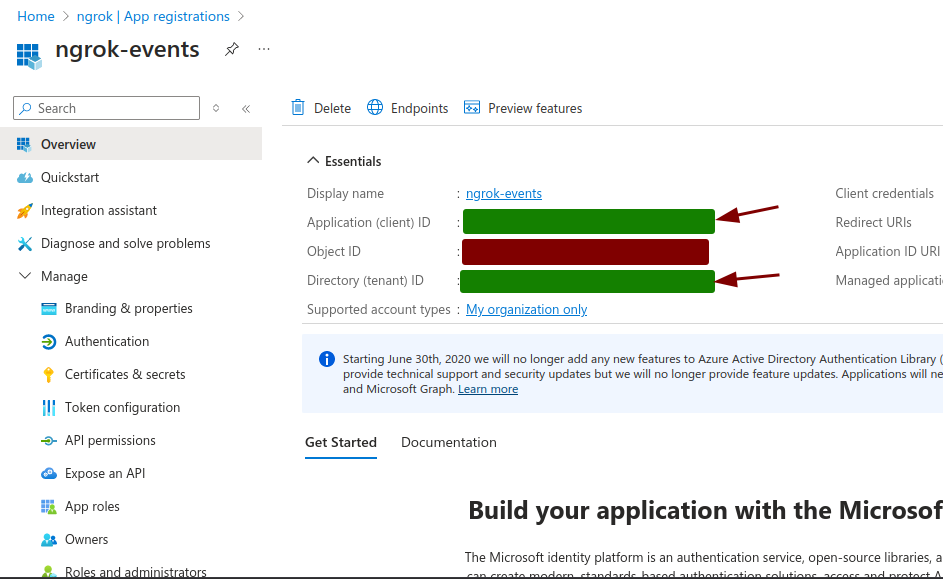
-
Navigate to Manage -> Certificates & secrets in the sidebar.
-
Click New client secret.
-
Fill in the description and expiry date with the desired values, before clicking Add.
-
Copy the secret value provided by Azure - this value will no longer be available once you navigate away.
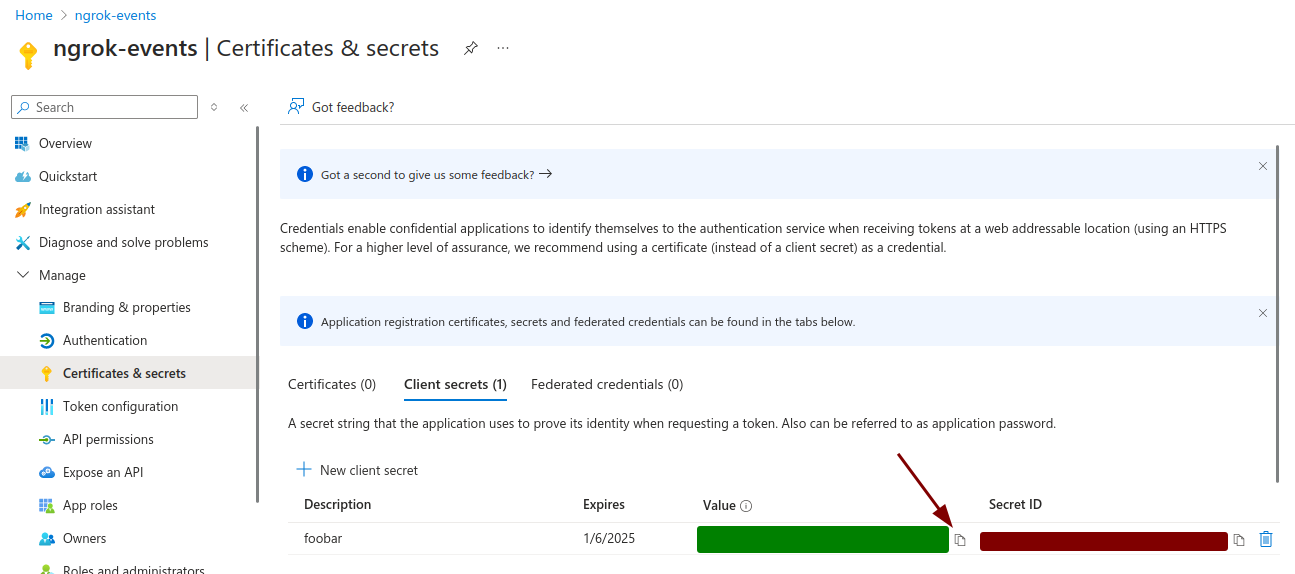
-
To gather the DCR persistent ID and stream name, navigate to Data collection rules using the top search bar.
-
Select the Data collection rule you created in Step 3.
-
In the Overview tab, copy the Immutable Id value.
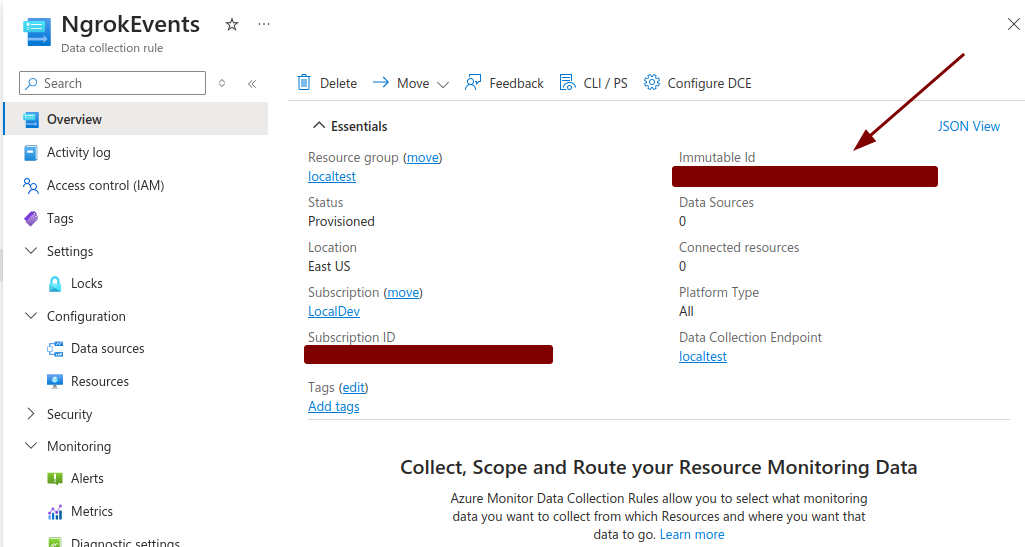
-
Navigate to Configuration -> Data sources in the sidebar.
-
Copy the Data source name, which should start with Custom_ and end with _CL. This is the DCR stream name.
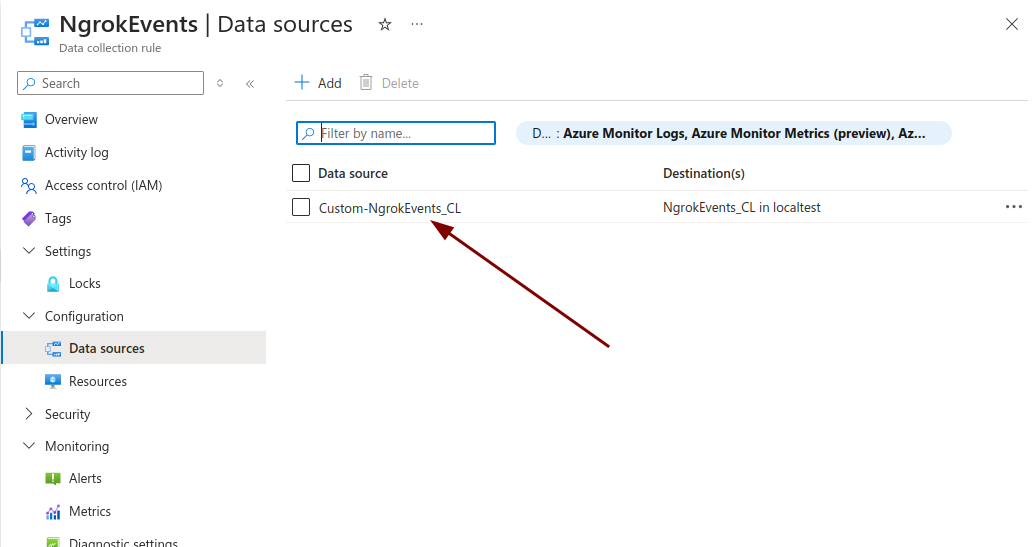
-
Finally, navigate to Data collection endpoints in the top search bar.
-
Select the Data collection endpoint you created in Step 2.
-
In the Overview tab, copy the Logs Ingestion URI.
You now have all the required data to create an event destination with ngrok!
Step 7: Create the new Event Destination in ngrok
At this point, you can choose to create the event destination through the ngrok Dashboard or via the ngrok API.
Creating through the ngrok Dashboard
-
Log into the ngrok Dashboard and navigate to Traffic Observability > Events Stream.
-
Create a new Event Subscription through the plus sign in the top left or open an existing one.
-
After adding one or more sources, select the Destinations tab and Add Destination
-
Select the Azure Logs Ingestion API option
-
Fill in the fields based on the values you collected in Step 6.
-
Click Send Test Event and look for an example event in your Azure Account. It may take a minute to show up due to propagation delays.
-
Click Done and save the new Event Subscription.
Creating via the ngrok API
-
Create an API key with ngrok. You can do this via the ngrok dashboard.
-
Using your Rest API tool of choice (cURL, Postman, etc.), you will run the following API calls.
-
To create the Azure logs ingestion event destination, run the following call:
Loading…
Copy the returned event destination ID (highlighted below).
Loading…
- To create an event subscription using the previously created event destination, run the following call
Loading…
After getting a 200 response, your event destination is successfully configured and subscribed to the set of events types you desire.